Microsoft Azure ExpressRoute / Microsoft ExpressRoute for Office 365
Step Propietario Descripción Preparation 1 Customer and Verizon You must be a Verizon Private IP customer to complete this activation process. If not, a Private IP connection must be established to at least one of your locations. As this component is probably the one with the longest deliverable timeframe, you should not proceed with the rest of the activation process until this step is completed. 2 Verizon You must have entitlements into Verizon Enterprise Center/Dynamic Network Manager which will allow access to your Secure Cloud Interconnect service.
This step could be completed once the Secure Cloud Interconnect order is entered.3 Customer Before proceeding with the Secure Cloud Interconnect Port activation, you must ensure that: - The IP ranges used with the Azure Virtual Network do not overlap with the IP ranges used on your Private IP VPN.
- You do not exceed the Max route prefixes supported by Microsoft private peering or Microsoft peering.
4 Customer If Microsoft peering (Office 365) is required, please check the Microsoft peering (Office 365) specific steps at the end of the document. Microsoft peering (Office 365) designs and features (which should be completed in cooperation with Microsoft) could have significant impact on Private IP address advertisement.
Note that although Office 365 is part of that same peering and needs to be activated the same way, Microsoft is still not providing an automatic approval for using Office 365 over ExpressRoute. That process has not changed. You still have to get Microsoft approvals before you can activate the Office 365 filters on the new peering interface.5 Customer and Verizon Verizon Account Team will work with you to provide you with a clear understating of Secure Cloud Interconnect NATing capabilities as well as the possible scenarios where you are required to provide public IP address for some of the features.
Please review the Secure Cloud Interconnect NAT section at the end of this document.6 Customer If you are planning to use Skype for Business with Office 365, you must mark your traffic for QoS handling. Please check the section on Skype for Business at the end of this document for the QoS marking to be used with each service. 7 Customer and Verizon If you have plans to use MSS Cloud Firewall as an addition to your Secure Cloud Interconnect service, please refer to the section on MSS Cloud Firewall for information on how to provision that service.
MSS Cloud Firewall has to be ordered at the same time as the Secure Cloud Interconnect port and cannot be added to an existing Secure Cloud Interconnect service.Ordering and Provisioning 1 Customer You establish a subscription to Azure with Microsoft. A subscription to Microsoft Azure is always required. 2 Verizon Verizon will coordinate with you to determine the type of Secure Cloud Interconnect connection(s) to be ordered based on which ExpressRoute peering(s) is required: - Private peering – Select Secure Cloud Interconnect Partner Service “Azure Private Peering”
- Microsoft peering – Select Secure Cloud Interconnect Partner Service “Azure Microsoft Peering”
- Microsoft peering Customer Provided NAT – Select Secure Cloud Interconnect Partner Service “Azure MS peering - Cust PROV NAT”
3 Customer and Verizon Determine the region(s)/locations in which the Secure Cloud Interconnect port(s) will be provisioned. 4 Customer You configure ExpressRoute with Microsoft. Following a successful configuration, Microsoft will provide you with an Azure Subscription ID and an ExpressRoute Service Key. - Each ExpressRoute connection will have its own Service Key. If you order multiple ExpressRoutes (e.g., one in San Jose and one in Ashburn), then two Service Keys will be provided, one for each ExpressRoute.
- A single Service Key can be used with the two peerings (Azure private and Microsoft) if those are configured over the same ExpressRoute connection.
5 Customer You provide the Azure Subscription ID and Service Keys to the Verizon Account Team. 6 Verizon The Verizon Account Team places the Secure Cloud Interconnect order using your Azure Subscription ID and ExpressRoute Service Key. The Subscription ID is entered in the ”CSP Customer ID” field and the Service Key in the “CSP Customer Service ID” field. 7 Customer You finalize the configuration of the services you ordered from Microsoft with Microsoft (O365, PaaS and/or IaaS). You have to ensure that the peering configured on the Microsoft platform matches the one selected with the Secure Cloud Interconnect port. 8 Customer and Verizon The Verizon Account Team, in consultation with you, identifies the appropriate time for activating the Secure Cloud Interconnect connection. 9 Customer Once the Secure Cloud Interconnect port is provisioned, you log into the Dynamic Network Manager, select the appropriate Secure Cloud Interconnect port, and tab on “Establish Connection.” The following fields will appear: 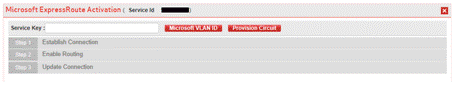
- In the Service Key field, enter the ExpressRoute Service Key.
- Click on “Microsoft VLAN ID” button. This will get the ExpressRoute S-tag from Microsoft via an API call. (Before proceeding to the next step, you must verify via the script window that a success notification has been received.).
- Click on “Provision Circuit.”
Once you establish a connection to Microsoft Peering over ExpressRoute, none of the services over that peering will be active. You will need to log into the Azure Portal and decide which of the available services to activate by updating the interface route filters. Please review that configuration with Microsoft. Once complete, the routes from those services will start to be advertised over the ExpressRoute connection. - Note: Each Secure Cloud Interconnect port is connected to a single peering (Private and Microsoft (Office 365).
10 Customer By default, the Private IP VPN entered with the Secure Cloud Interconnect order is connected to the Secure Cloud Interconnect port. If you want to add additional VPNs and have a standard Secure Cloud Interconnect design, you can use the Dynamic Network Manager to add one or more of your Private IP VPNs to the Secure Cloud Interconnect port using the Add/Remove VPN menu. However, if you have a non-standard Secure Cloud Interconnect design, contact the Verizon Account Team before proceeding with this step.
Note: When you add or remove Private IP VPNs to a Secure Cloud Interconnect port to ensure that the IP addresses of the Private IP VPNs don’t overlap and that the total number of Private IP prefixes does not exceed the MAX number specified in the VPNs. In the latter case, you must contact the Verizon Account Team and request an increase to that MAX number.
11 Customer Verify in Dynamic Network Manager and the ExpressRoute portal that your Private IP network is connected to ExpressRoute. 12 Check the “Shutting Down the Secure Cloud Interconnect Port” section at the end of this document for the steps to be taken if the port to shut down the port. Office 365 Specific – Microsoft Peering 1 Customer In the design stage, determine with your Microsoft resources whether your Office 365 design requires traffic originating from Microsoft Office 365 and designated to selected customer servers via ExpressRoute/Secure Cloud Interconnect. Examples of these selected servers include an ADFS proxy if Office 365 single sign-on is implemented with on-prem Active Directory authentication Exchange Hybrid, etc. Not all Office 365 scenarios require this step.
You may have to identify the public IP prefix (IP range + Subnet mask) for these servers. Microsoft requires that these IP prefix(es) be public in nature, not private (RFC1918).
These public IP prefix(es) must be advertised to the Private IP VPN that will be associated with Secure Cloud Interconnect. Your Private IP design should allow for this factor.
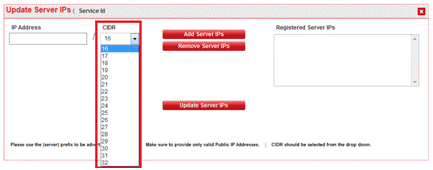
The Dynamic Network Manager portal currently supports subnet mask from /16 - /32 under “Update Server IPs.”2 Customer You must submit a Microsoft Support Ticket to get the server IP addresses whitelisted (pre-validated) before adding the public IP’s in Dynamic Network Manager. Whitelisting must take place prior to activation through the Verizon portal. - The Microsoft Support Ticket should include the following information: Your server public IP prefix determined in Secure Cloud Interconnect planning stage (refer to Step 1)
- Microsoft ExpressRoute Key for the location where this public IP prefix will be leaked to Microsoft
- Microsoft Azure Subscription ID
Microsoft could require additional information.3 Customer Once Secure Cloud Interconnect is provisioned on Verizon and appears in Dynamic Network Manager, these public IP prefix(es) have to be leaked to Microsoft. (This is enabled for Non-Enhanced Security customers.) - On the Dynamic Network Manager portal, select the appropriate Secure Cloud Interconnect and then navigate to the “View/Edit Servers” page.
- Add the IP addresses of the servers on that page with the exact match of IP subnet and subnet mask advertised to Private IP VPN.
- Once all the addresses are added, click “Update Server IPs.”
- When this step is completed, switch to the Secure Cloud Interconnect Activation page, and click on “Update BGP Peering.”
- This action will allow the Secure Cloud Interconnect Firewall to leak these public IP prefix(es) to Microsoft peering of ExpressRoute.
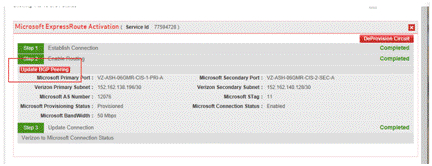
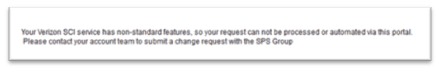
Note: For Office 365 customers with Enhanced Security who wish to add public IP prefixes, the “View/Edit Servers” functionality is disabled, and you need to contact your Verizon Account Team to submit a change request with the MSS Cloud Firewall Enhanced Security team.
4 Customer and Verizon Microsoft peering Office 365 advertises 900 additional routes to your route tables. Because the standard default number of routes for a Private IP customer is 1250, adding a Secure Cloud Interconnect connection with Microsoft ExpressRoute for Office 365 may require an increase to the number of MAX routes on the Private IP VPN that is linked into the Secure Cloud Interconnect Cloud to support the Microsoft ExpressRoute for Office 365 environment.
If your existing private network does not have enough MAX routes configured to account for the additional routes, this will need to be changed as part of the final configuration of the Secure Cloud Interconnect connection. You need to make the request to the Verizon Account Team to initiate the increase to the MAX route setting to mitigate this concern.5 Customer ExpressRoute Premium is required for supporting Office 365.Check with your Microsoft contact. Skype For Business 1 Customer QoS configuration is required with Skype for Business, where various workloads require differentiated QoS treatment.
The following table provides a list of DSCP markings used by Skype for Business.TRAFFIC CLASS TREATMENT (DSCP MARKING) SKYPE FOR BUSINESS WORKLOADS Voz EF (46) Skype / Lync voice Interactive AF41 (34) Video AF21 (18) App sharing CS3 (24) SIP signaling De forma predeterminada AF11 (10) Transferencia de archivos CS0 (0) ¿Algo más? 2 Customer Review the Microsoft Skype for Business page for the latest updates and other requirements associated with that service. 3 Verizon and Customer If you are planning to use Voice with Skype for Business, Verizon and you must ensure that your Private IP service has an EF component. 4 Verizon Verizon will honor all QoS marking in the Private IP network and will pass the marking to Microsoft. Microsoft will honor the marking and mark your traffic as “only for Skype for Business.” All other Microsoft services will ignore the QoS marking. Secure Cloud Interconnect NAT 1 Verizon and Customer When you use services from Microsoft Peering (Office 365, CRM, etc.), you are required to use public IP addresses to communicate with Microsoft.
Verizon Provided NAT
For outbound traffic (from Verizon to Microsoft), Verizon will provide Source NATing functionality that NATs the source address of all outbound traffic. Verizon will provide the public IP addresses required for the outbound NATing.
For inbound traffic (from Microsoft to Verizon which is possible only with O365), Microsoft mandates that public IP addresses be provided for servers that Microsoft needs to access. It is your responsibility to provide those public IP addresses. Verizon will not support static NATing for those public addresses but will configure our firewalls to leak those addresses to Microsoft.
Please check the Office 365 specific steps earlier in this document for how to provide and configure those addresses.Customer Customer Provided NAT
As part of our standard product offering for non-VPC services to a CSP, Verizon provides the necessary NAT feature and functionality. However, if you prefer, you may be able to provide your own NAT IP addresses instead of using Verizon’s public IP prefixes.
Customer Provided NAT feature enablement will remove the insertion of Verizon’s NAT functionality for non-VPC connections to the CSP. This provides you additional control of your network and communication to the CSP.
Please note that with the Customer Provided NAT feature, you will be responsible for providing the necessary public IP addresses required for the NAT feature and “whitelisting” those addresses with your CSP. For Microsoft Peering (including Office365), Microsoft may initiate a session from their cloud into your network.
As such, NATing capability will be required in both directions if you provide your own NAT functionality.
Note: With Customer Provided NAT, you are responsible for working with the cloud provider to ensure all NATing functionality is cared for. Verizon cannot manage your NATing with the CSP. You cannot have a mix of Verizon and Customer NATing on a single Secure Cloud Interconnect connection.
Note: If you choose to revert back to the Verizon-provided NAT, you would need to disconnect the service and reinstall the service with NAT functionality. Ask your Verizon Account Team for details.2 Verizon At the Secure Cloud Interconnect provisioning time, Verizon will select a single, permanent/32 address and assign it to you. 3 Customer and Verizon Microsoft Peering (Office 365) traffic that is part of a connection initiated by Microsoft cloud services towards your network must be SNATed before you access your network.
Verizon will provide that SNAT functionality, but you must expect to see Verizon NAT addresses advertised on your VRF (Private IP VPN).
The IP address used with that NATing will be available via the Dynamic Network Manager portal4 Customer The NAT rules specified by Microsoft can be reviewed on the Azure webpage. MSS Cloud Firewall 1 Verizon and Customer MSS Cloud Firewall has to be ordered at the same time as the Secure Cloud Interconnect port. MSS Cloud Firewall cannot be added to Secure Cloud Interconnect once the Secure Cloud Interconnect port is activated. 2 Verizon and Customer You will need to provide Verizon with the firewall rules. Verizon will then activate the port. 3 Customer You have “Read” privileges to MSS Cloud Firewall. You do not have “Write” privileges. You can change the Firewall rules by notifying Verizon or entering the changes in the MSS Cloud Firewall portal. “Shutting Down” the Secure Cloud Interconnect Port 1 Customer or Verizon To “administratively shut down” the port you or your Verizon Account Team would log into Dynamic Network Manager and selects the Secure Cloud Interconnect port.
As highlighted, click on the pen following the “Modify Admin Status” field.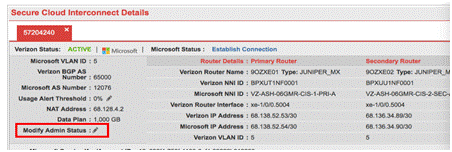
2 Customer or Verizon The following screen shot shows the page that will open once the “Modify Admin Status” pen is clicked.
The Shutdown or No Shutdown of the port can be done through the “New Admin Status” drop down menu.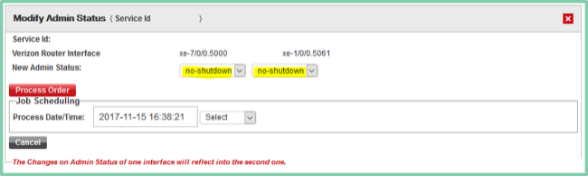
Connection Characteristics 1 Customer FYI For Azure private peering, Verizon Private IP private AS 65000 is used. For Microsoft peering (Office 365 and CRM Online), a public AS# is required and Verizon uses AS 1684.
Microsoft uses AS 12076 for Azure private and Microsoft peering and have reserved ASNs from 65515 to 65520 for internal use.
Both 16 and 32-bit AS numbers are supported.
Services and/or features are not available in all countries/locations, and may be procured from in-country providers in select countries. We continue to expand our service availability around the world. Please consult your Verizon representative for service availability. Contact us.